
How To Secure Your Business IT In Melbourne
I'm sure you agree with me when I say that there is not a week that goes by when you don't see an email or hear about cybersecurity and how cybercriminals have bled another Business dry of money.
The threat is constant, evolving, and increasingly sophisticated.
In this comprehensive guide, I'm going to outline the most effective ways to secure your IT systems in your business and your personal life.
From small startups to established businesses, these principles apply universally and can save you from becoming the next cybersecurity headline.
This is not going to be too technical, and you'll discover why implementing robust security measures need not cost a fortune.
In fact, some of the most effective strategies require minimal financial investment but can yield tremendous protection for your business.
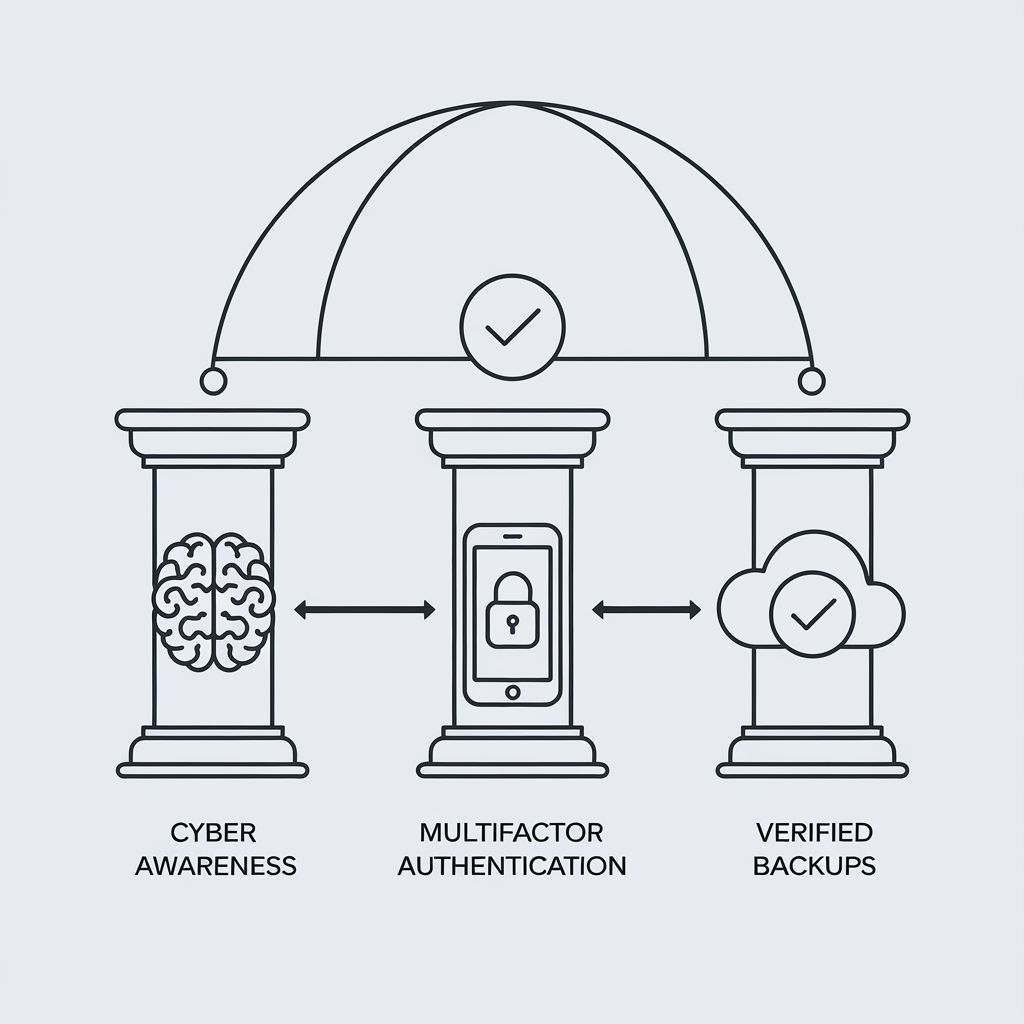
The Three Pillars of Effective IT Security For Your Business
Building A Culture Of Cyber Awareness
People are by far the weakest link in any small business's IT systems.
You could invest hundreds or even thousands in a new IT security system, and it could quite easily be bypassed by one of your colleagues who does not have an awareness of what to look out for in a classic phishing email.
Luckily, the solution is simple, and it does not involve significant financial investment.
Time is the only investment.
Just make sure you are running regular lunch and learns with your current technology provider.
This can be as quick as a half-hour session to go over the latest threats that may be landing in your inbox.
Your IT/Technology provider will have a good idea of what this looks like as they're dealing with cyber threats daily and are "in the know" on what to look out for.
Creating an Effective Cyber Training Program
To maximise the effectiveness of your cyber awareness efforts, consider implementing these practices:
- Regular Training Sessions: Schedule monthly updates rather than one annual training that's quickly forgotten.
- Real-World Simulations: Conduct mock phishing campaigns to test employee awareness and provide immediate feedback.
- Clear Reporting Channels: Ensure everyone knows exactly how to report suspicious emails or potential security incidents.
- Recognition Programs: Acknowledge and reward staff who identify and properly report potential threats.
Research shows that organisations with regular cyber awareness training experience up to 70% fewer successful cyberattacks.
This single practice could be your most cost-effective security measure.
Enforce Multifactor Authentication
Those in the know call this MFA or 2FA, but we're keeping this simple, so multifactor authentication is a little more understandable.
It's making sure any of the cloud services you're currently utilising are protected with two passwords and not just one.
This is implemented by having a standard password and a secondary password which is authorized by your smartphone.
Running either an app on your phone or a text message that asks you merely to approve/deny the login to your cloud service when you are at the login page.
This is by far one of the best methods to protect against hackers as most hacks over the last 12 months have been to cloud services by cybercriminals pretending to log you into a genuine cloud service.
Without access to your smartphone, they don't have a chance of bypassing this multifactor authentication security.
Implementing MFA Across Your Business Technology In Melbourne
When rolling out multifactor authentication, consider these best practices:
- Start with Critical Systems: Begin with your most sensitive applications like financial systems, email, and customer databases.
- Choose the Right Method: Authenticator apps are generally more secure than SMS-based authentication.
- Provide Clear Instructions: Create simple step-by-step guides for all employees to follow.
- Have Backup Methods: Ensure users have backup authentication options in case they lose their primary device.
Studies reveal that MFA can block over 99.9% of automated attacks, making it one of the most powerful security tools available to businesses of any size.
Verify Your Backup Strategy
When I tell you about this next tip, you're not going to believe how obvious it seems. If your IT systems do become victim to an attack, you may find that the only way to recover your systems is by changing passwords and restoring your files from a backup.
We've seen this one too many times to count from clients coming over to us in the past when a ransom is asked for. Their current IT provider fails at the most crucial stage and that is by backing up the company data correctly.
While the business may have backup software in place and it's turned on, no one at the IT company has checked to see if files and data can be restored from the backup. Such a simple thing that is missed out. Please make sure that you can restore from a recent backup.
Building a Bulletproof Backup Strategy
An effective backup strategy includes:
- Regular Testing: Schedule quarterly restore tests to ensure your backups actually work.
- Follow the 3-2-1 Rule: Keep three copies of your data on two different types of media with one copy stored off-site.
- Automated Verification: Implement systems that automatically verify successful backups and alert you to failures.
- Isolated Backups: Keep some backups disconnected from your network to prevent them from being compromised in a ransomware attack.
Remember: A backup you haven't tested is a backup you don't have.
Additional Security Measures For Your Business In Melbourne
Implement Strong Password Policies
While multifactor authentication provides excellent protection, the foundation starts with strong password practices:
- Require complex passwords of at least 12 characters
- Implement password managers to help employees maintain unique passwords
- Set reasonable password expiration policies that don't encourage poor practices
- Consider passwordless authentication technologies where appropriate
Keep Systems Updated
Cybercriminals frequently exploit known vulnerabilities in outdated software:
- Establish a regular patching schedule for all systems
- Prioritise critical security updates
- Consider automated patching solutions for consistent implementation
- Document exceptions where patching might affect system stability
Network Security Essentials For Business Owners
Your network is the highway to your data, and it needs appropriate guardrails:
- Implement next-generation firewalls that can inspect encrypted traffic
- Set up network segmentation to contain potential breaches
- Deploy intrusion detection systems to alert you to suspicious activity
- Regularly scan for unauthorized devices on your network
Third-Party Risk Management
Your security is only as strong as your weakest vendor:
- Create a vendor security assessment process
- Include security requirements in all contracts
- Regularly review third-party access permissions
- Establish incident response procedures that include vendor involvement
Implementing Security on a Budget For Your Business

One common misconception is that good cybersecurity requires massive investment.
While business-grade solutions can be expensive, there are numerous ways to significantly improve your security posture without breaking the bank:
Free and Low-Cost Security Tools
- Open-source security software often provides robust protection
- Cloud providers include many security features in their basic offerings
- Government agencies provide free cybersecurity resources for small businesses
- Community threat intelligence sharing can provide early warnings at no cost
Strategic Security Investments
When you do need to invest in security, focus on:
- Areas where your risk assessment reveals the greatest vulnerabilities
- Solutions that protect your most valuable assets
- Tools that provide the greatest coverage for your specific environment
- Managed services that give you enterprise-level protection at a fraction of the cost
Creating Your Business Security Roadmap
Implementing all these measures at once can be overwhelming. Instead, take a methodical approach:
- Assessment: Understand your current security posture and most critical risks
- Prioritisation: Address the highest-risk, lowest-effort improvements first
- Implementation: Roll out changes in phases to minimize disruption
- Verification: Test that your security measures are working as expected
- Continuous Improvement: Regularly review and update your security strategy
Security as a Business Enabler
These are just some of the most obvious tips I've outlined in this article.
If you'd like to hear about some other crucial steps you can implement in your business that don't require massive investment, then please connect with me.
Remember that good security isn't just about preventing bad things from happening – it's about enabling your business to operate with confidence.
By implementing these measures, you're not just protecting your data; you're building trust with customers, meeting regulatory requirements, and creating a foundation for sustainable growth.
Thesedays security isn't optional – it's essential.
And with the right approach, you can secure your company's IT like a boss, without requiring a boss's budget.



